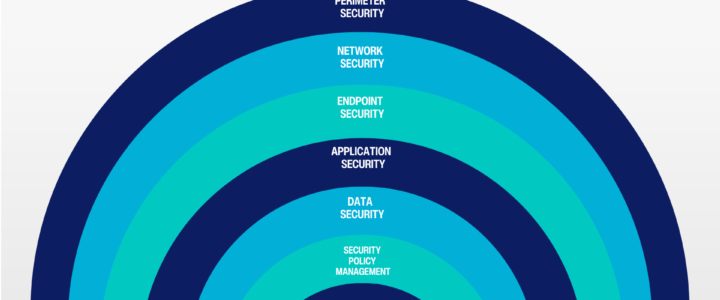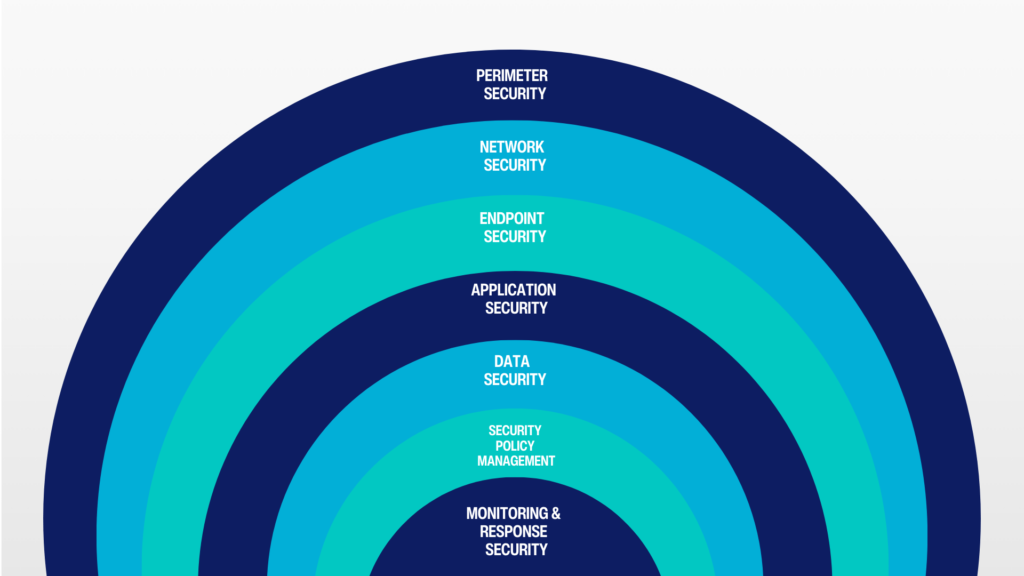
Cyber threats are evolving rapidly, making cybersecurity a top priority for IT leaders. Organizations must balance robust security measures with budget constraints while navigating a crowded market of security solutions. The seven layers of cybersecurity provide a comprehensive framework for protecting digital assets, but how can you maximize security while optimizing costs?
In this guide, we break down the seven layers of cybersecurity to help you identify the most critical areas for investment and ensure your budget is allocated effectively to defend against cyber threats.
1. Perimeter Security
Your first line of defense against cyberattacks, perimeter security protects your network from external threats using firewalls, intrusion detection systems (IDS), and secure web gateways.
Cost-Effective Tips: | • Choose scalable firewalls and IDS solutions with integrated threat detection and automated response capabilities • Implement Zero Trust security principles to enhance perimeter defense. |
2. Network Security
Safeguarding your internal network from unauthorized access and cyber threats is essential. Implement network firewalls, encryption, and intrusion prevention systems (IPS) to protect sensitive data and ensure network integrity.
Cost-Effective Tips: | • Invest in unified network security solutions that combine firewall, VPN, and monitoring features • Prioritize end-to-end encryption without sacrificing performance. |
3. Endpoint Security
Endpoints, including laptops, smartphones, and IoT devices, are common attack vectors. Advanced endpoint detection and response (EDR), antivirus software, and device encryption help mitigate risks.
Cost-Effective Tips: | • Deploy endpoint security solutions with centralized management to streamline protection across all devices • Implement Bring Your Own Device (BYOD) policies with strict security protocols. |
4. Application Security
Protect software applications from vulnerabilities throughout their lifecycle with secure coding practices, regular penetration testing, and application firewalls.
Cost-Effective Tips: | • Use automated code analysis tools to detect vulnerabilities early in development • Leverage open-source encryption solutions for cost-effective protection. |
5. Data Security
Data is a prime target for cybercriminals. Encryption, access controls, and cloud security measures help prevent unauthorized access and data breaches.
Cost-Effective Tips: | • Utilize built-in cloud encryption services for data protection • Automate data backups and disaster recovery plans to mitigate ransomware risks. |
6. Security Policy Management
A well-defined cybersecurity policy helps mitigate human error and strengthen organizational security. Effective governance, compliance measures, and employee training play crucial roles.
Cost-Effective Tips: | • Use single-pass architecture to distribute security policies efficiently across all endpoints • Implement security awareness training to educate employees on phishing and social engineering threats. |
7. Monitoring & Response Security
Continuous monitoring and a proactive incident response plan ensure early threat detection and rapid mitigation of cyberattacks.
Cost-Effective Tips: | • Consider Security Information and Event Management (SIEM) solutions with AI-powered threat detection • Opt for managed security services to gain 24/7 threat monitoring without the overhead costs of an in-house SOC. |
Strengthen Your Cybersecurity with Expert Guidance
Balancing cybersecurity investments with financial constraints is possible when you prioritize critical security layers and leverage cost-effective solutions. A strong security posture is essential—not a luxury.
At Technology Navigation, we help businesses assess cybersecurity risks, implement tailored security solutions, and navigate complex vendor landscapes. Contact us today to strengthen your cybersecurity strategy and protect your organization from evolving threats.